How to Spot Tech Scammers
Tech Scammers in the Wild
Tech scammers are sneaky and aggressive. You are browsing the internet when all of a sudden…
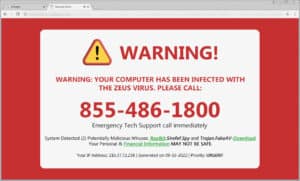
The browser you are using is locked and you can’t to exit out. The screen is completely red with flashing alarms. The text states your credit card/personal information is being stolen by hackers or that your computer has Malware. You panic. So you call the number to find out that they are demanding $300, $600, or even $900 to fix your computer and/or to provide life-time support. They are almost yelling at you and demanding you listen to them. Then, they request access to your computer remotely to remove the malware currently infesting itself on your computer.
There is just one issue: the person on the other side is a criminal.
What Now?
Now they have control of your computer. They can see your files, and possibly your saved passwords, accounts, and more. At the very least, they can prevent you from doing anything to your computer.
What if you don’t pay? Sometimes, if you don’t pay, they take your computer for ransom.
How Big Are Tech Scammers?
Tech scam operations grew so quickly in America that it is now recognized by the Federal Trade Commission as a threat against Privacy, Identity, and Online Security. These scams have origins that date back to the days of AOL (America Online) with the Nigerian Prince Email Scam. You might remember that email claiming a prince needs your bank account information to deposit millions of dollars in it to help him get to America. Now, the tech scam operations have become more intricate by scammers pretending to be Microsoft or Apple certified technicians. Protecting yourself online has never been more vital. So how do you spot a tech scammer? Here are some clear signs that a tech scammer is trying to scam you.
1. BROWSER LOCK!
Strategically placed fake warnings online are traps. They pop up as you navigate your web browser to the website accidentally and state that your computer is infected with every piece of malware under the sun. This is the main resource/scam Fake I.T, or Tech Scammers, use today. Tech Scammers are people that pretend to be Microsoft Tech Support or Apple Tech Support. These pop-ups hi-jack your browser in a sense by limiting your access to the browser and not allowing you to use the “back” button. In doing so, they intentionally do not allow you to use your browser until you either enter in your information or click on a link to download. These pop-ups may look legitimate, but they are not. However, do not panic. Your computer is more than likely not infected with any malware from the website.
Tech Scammers: Think About it This Way…
You’re walking your dog down Main Street in the small town of Internetville. It’s a beautiful day in Internetville! The sun is out, there’s a slight breeze, and your dog is as happy as it can be smelling all the flowers. As you walk past a shop, you see an advertisement for great deals on shoes you really like. All of a sudden, a veterinarian with a microphone jumps out from behind a corner with alarms and sirens blaring.
The veterinarian is yelling at you frantically through the microphone. “Your Dog has five hundred dog viruses! I am a certified veterinarian! I must perform immediate dog-virus removals! The Dog-Virus removals will cost three-hundred-thousand dollars for lifetime dog-virus removal support!” You ask yourself if this veterinarian is legitimate. So you politely decline and say you will take your dog to your known veterinarian. But then the “veterinarian” grabs your dog, holds him in the air, then yells at your dog through the microphone, “Your dog has many virus, call 1888-545-5555 for dog virus removal.”
2. Pop-Up Scams
Clear signs of Pop-Up Scams are:
- Demanding payment before work
- Locking your browser so you can’t leave the site
- Telling you to call a number like 1-888, 1-866, 1-855, or sometimes a 1-800 number
- Over-zealous flashing lights and alert noises (like you would find in movies)
- Telling you hackers are currently stealing your credit cards or other information
How to avoid Pop-Up Scams:
- Do not click links in emails from people you do not know
- Do not click random/extraneous links on websites that redirect you to other pages
- Do not click advertisements
- Understand your location in the Browser URL (i.e. if you want to be on Google make sure the URL is https://www.google.com)
- Research unknown sites by looking them up in Google to see if they are malicious or not
3. COLD CALLS
If you receive a phone call from Microsoft out-of-the-blue, you are either Bill Gates or it is a scam. The Caller ID may also say “Microsoft” or “Tech Support”. Companies such as Microsoft, Apple, Dell, etc. won’t waste time or money to call you if your computer is infected. In actuality, if you are having computer related problems, you will most likely have call them.
In the past, tech scam operations were in primarily western countries. However, new scamming operations are popping up in Florida. Furthermore, the scammer may use specific terminology related to malware on your computer. Again, there is no way for a person to know that your computer is infected with malware unless they are in it. Lastly, if you do not know the number of who is calling you, it’s best to just allow them to leave a message in your voice mailbox.
Additionally, this may be off-topic from tech scammers, but other scam operations have claimed to be the IRS, police, and debt collectors.
Clear signs of Cold Call Scams are:
- Caller ID displays “Microsoft” or “Tech Support”
- The person sounds like an automated voice message
- The person is demanding payment, but does not have justification to be collecting debts
- They claim your computer is infected without seeing it
- They ask you to navigate to a specific website to download their “Special” tools
How to avoid Cold Call Scams:
- Do not answer your phone for unrecognized numbers
- Do not give out personal information over the phone to un-trusted sources. This information is shared and used again amongst scammers
- Block numbers of scammers that have been calling you
- Research online the phone number that has been calling you. Chances are the scammers are on a “Do Not Answer” list where other users share their experiences with the scammers
TO SUM THINGS UP WITH TECH SCAMMERS
Summing up, scammers are notorious from impersonating legitimate businesses in order to steal money out of people’s wallets. The best way to defend yourself is by trusting your gut. So if you feel that it may be a scammer on the other end of the phone, then it may very well be. The best way to find out if a scammer is harassing you is to just Google search the phone number of the Pop-Up or the phone number calling you. Chances are other people have dealt with the same scammer prior and are able to validate if it is a scammer or not.



